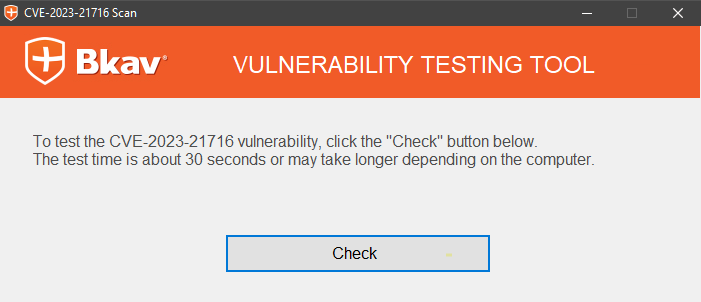
How cve-check-tool resolve custom package name assigned to a package in a recipe? · Issue #59 · clearlinux/cve-check-tool · GitHub
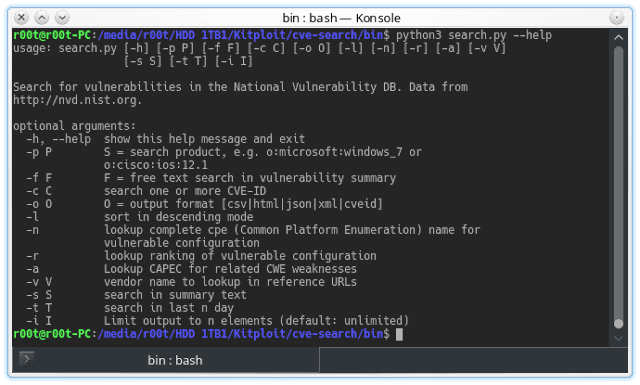
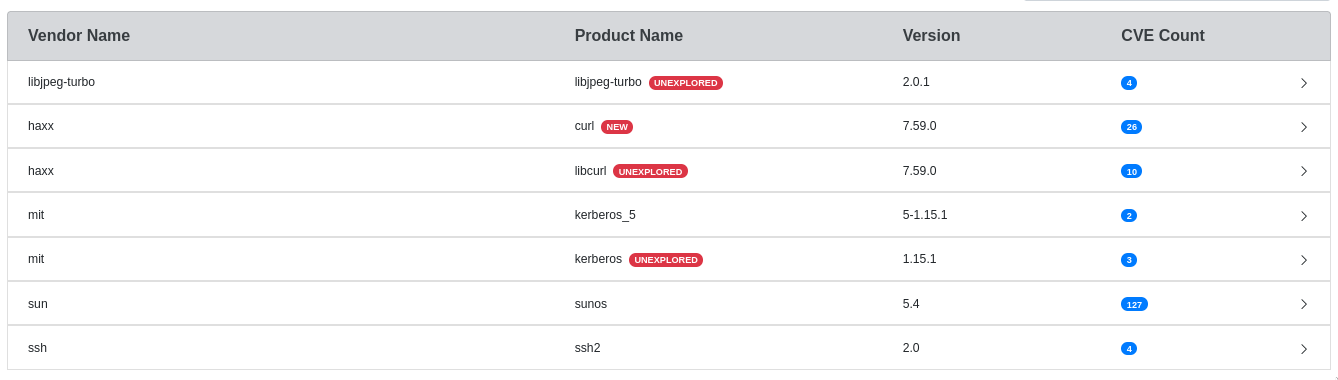
GitHub - intel/cve-bin-tool: The CVE Binary Tool helps you determine if your system includes known vulnerabilities. You can scan binaries for over 200 common, vulnerable components (openssl, libpng, libxml2, expat and others),
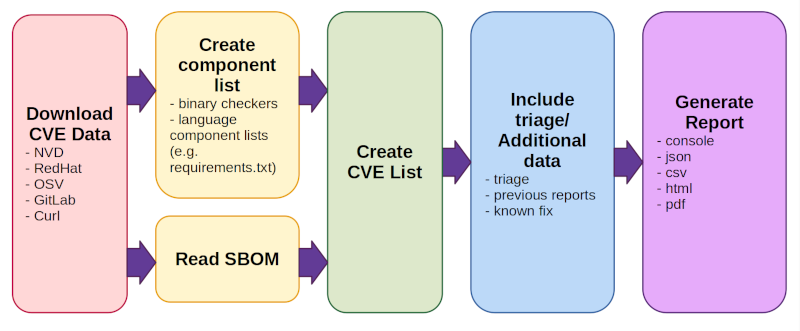
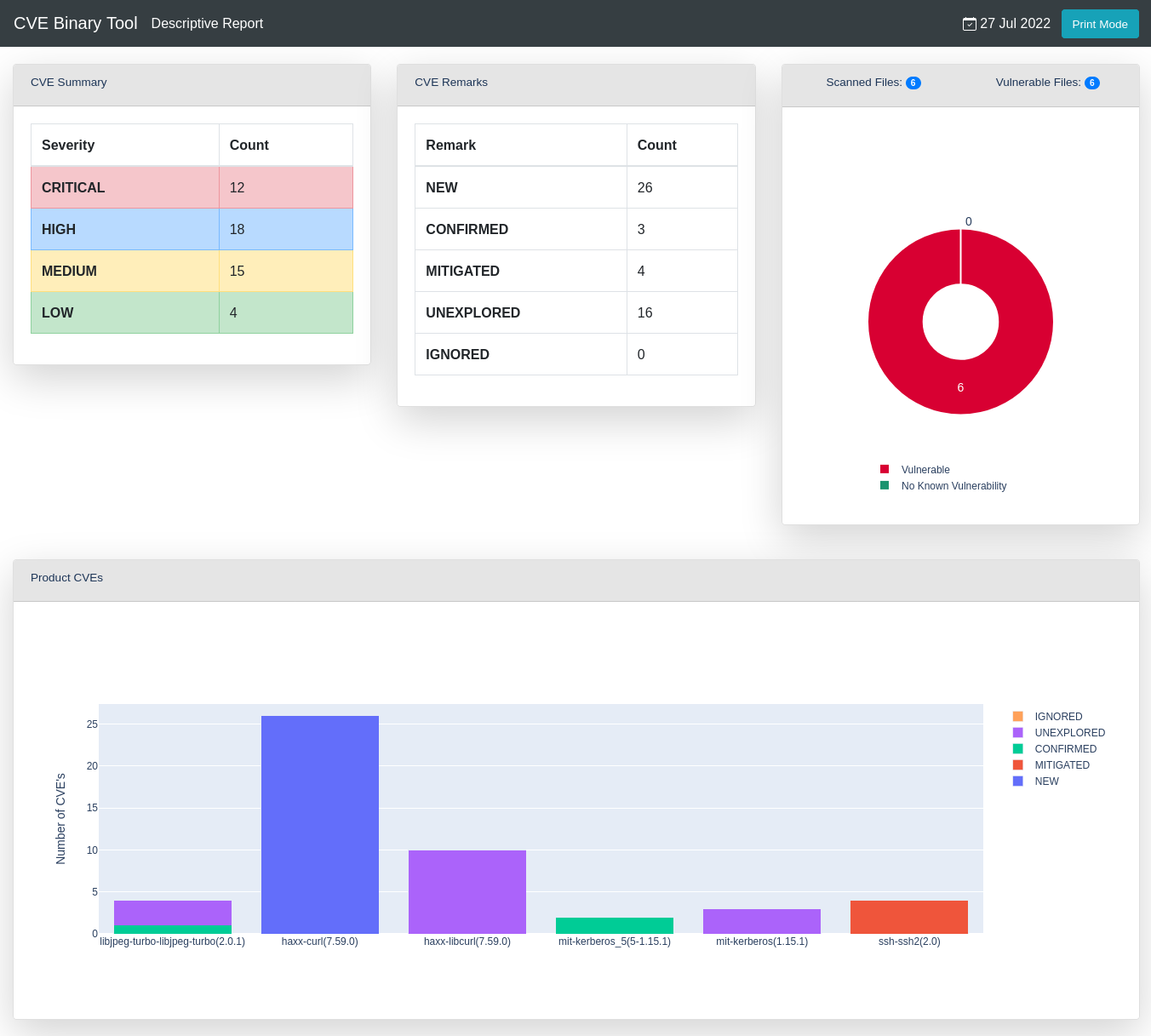
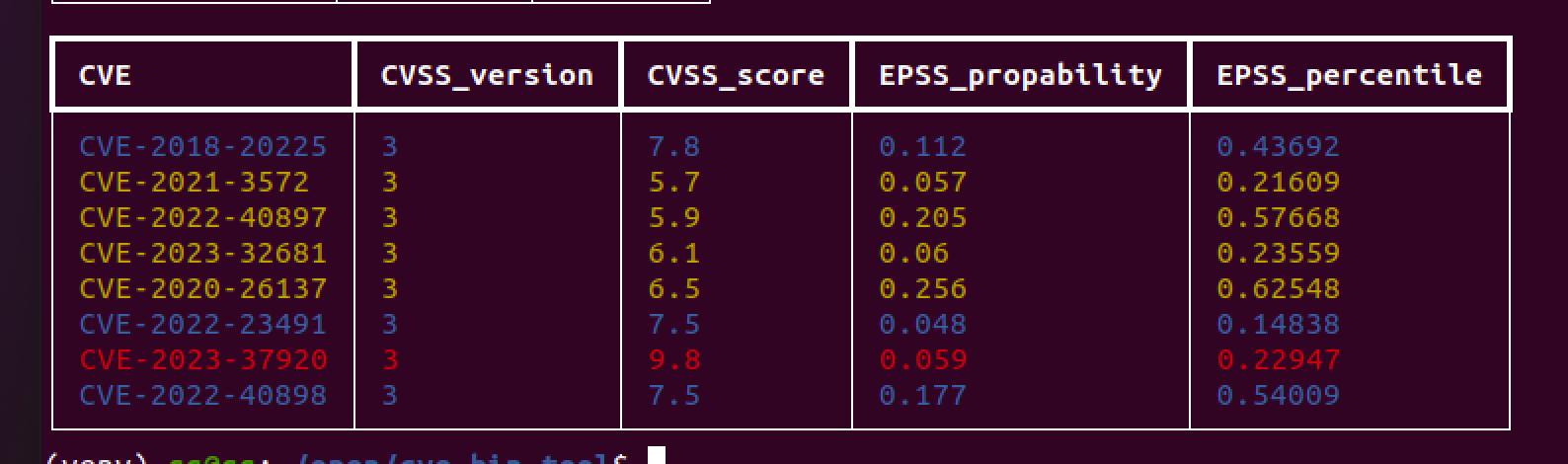
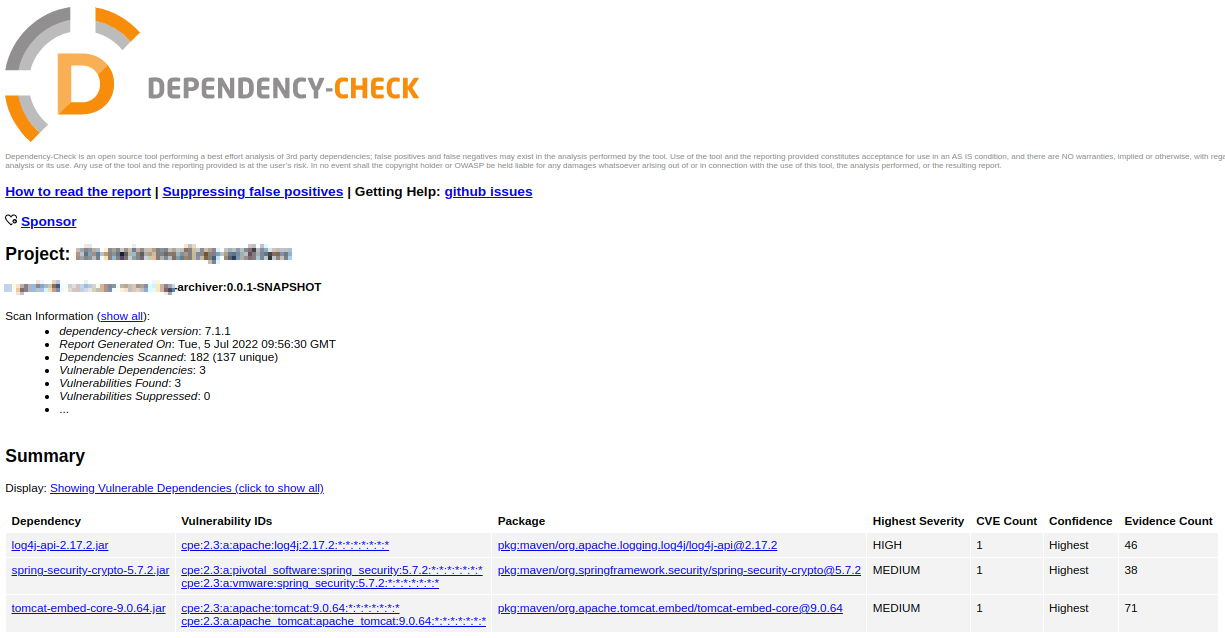
GitHub - intel/cve-bin-tool: The CVE Binary Tool helps you determine if your system includes known vulnerabilities. You can scan binaries for over 200 common, vulnerable components (openssl, libpng, libxml2, expat and others),