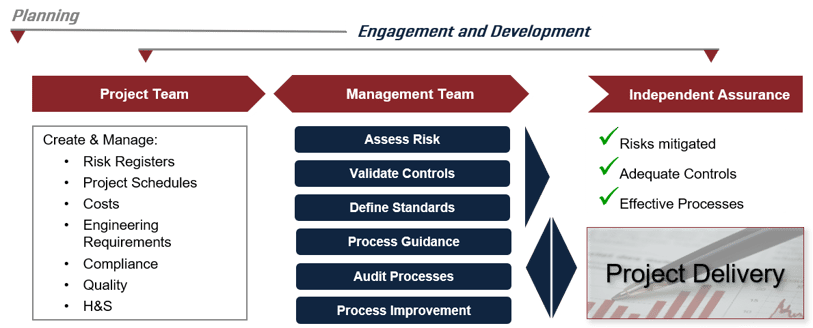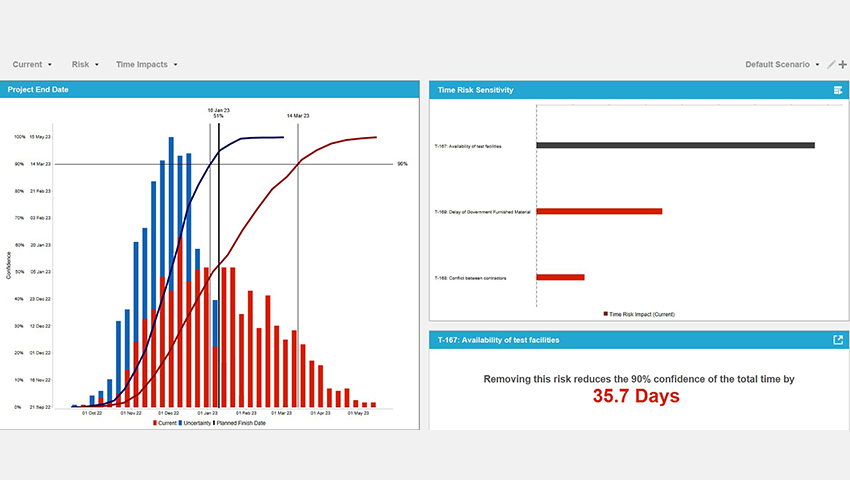
Risk Decisions' Predict! software is strengthening risk management in Australian defence - Defence Connect
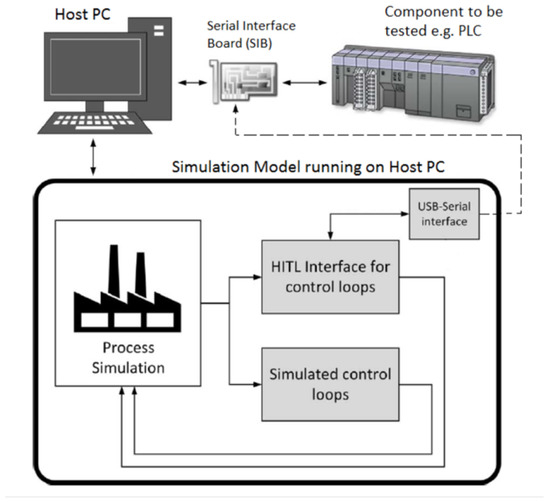
JSAN | Free Full-Text | Preliminaries of Orthogonal Layered Defence Using Functional and Assurance Controls in Industrial Control Systems



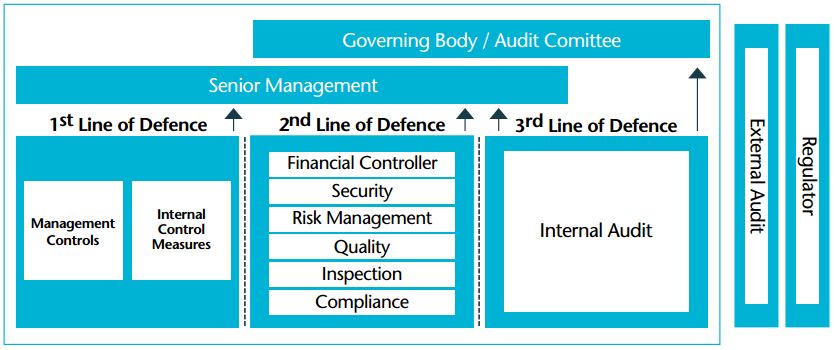




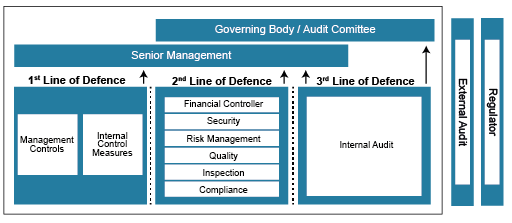





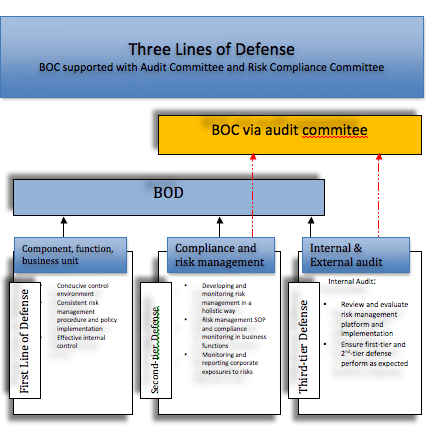

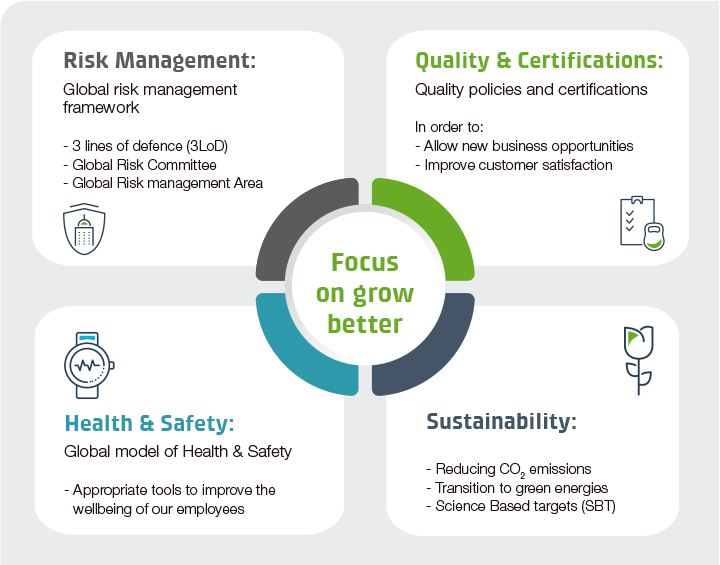


.png)